Definition of Phishing
A phishing attack uses social engineering for identity theft. A type of cyberattack that is set to get confidential and sensitive information out of users.
Phishing requires hackers to send spoofed emails or texts (smishing) in the name of a legitimate organization to victims. This tricks them into clicking on a malicious link, or attachment, and out their personal information.
Phishing scams also use software or security vulnerabilities to install malware on the target user’s computer. In all cases, the human factor plays a key role in the successful phishing attempts of these cybercriminals.
Yet, phishing attacks are not limited to email phishing. Phishers use SMS text messages (smishing) and voice messages (vishing) too, by posing as a legitimate organization. Techniques worked to trick victims to win over their information.
According to the Verizon Data Breach Report (DBIR) 2021, 36% of breaches involve phishing attacks.
Definition of pharming
Pharming is sometimes referred to as “phishing without a lure.”
It’s a cyberattack that involves installing malicious code or malware on a server to misdirect or automatically redirect users to fake replica websites without the user being aware. These spoofed websites look like the actual sites to trick the user to get personal information.
While the method is different from phishing, the goals are the same.
Pharming still aims to steal personal information (login credentials, financial information, personal details about the person, etc.). A user can fall victim to pharming even if they click on an authentic link if a hacker hijacks the website’s domain name system (DNS).
As in a phishing attack, the pharming attack is equally dangerous for users online. In this social engineering scam, the chances of recognizing the danger are slim. The threat is hidden, and often a user won’t know if the website is hijacked before handing over the personal request information.
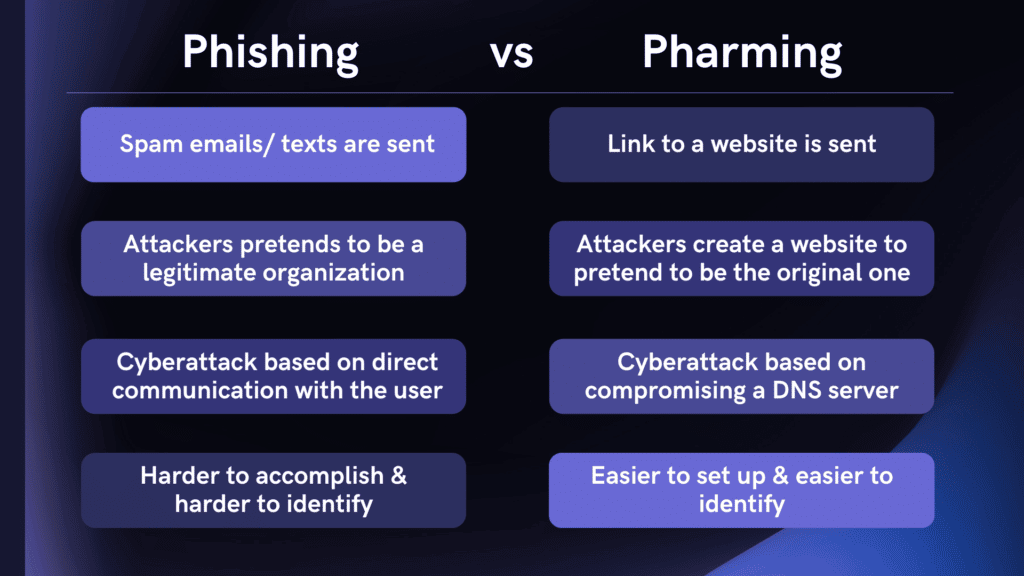
Pharming scams are executed by misusing the DNS as the primary weapon, while phishing attacks use spoofed websites that seem legitimate to users.
Phishing uses baits like fake links, while pharming uses DNS server redirects to direct users to a fake replica website.
What is the difference between Phishing and Pharming?
In phishing, an attacker acquires sensitive information from users through communications outreach, luring targets to act on it.
Phishing supersets the same behaviors across different communications channels (e.g., email phishing, SMS smishing, VoIP vishing and fax phishing – phaxing).
In phishing, an attacker uses communication and sends a link to a spoofed website to collect personal information from users. A phishing scam is relatively easy to set up, but often, it may be easy for a wary user to identify a phish.
In pharming, an attacker leverages DNS to redirect a user to a fake website, where they are tricked into entering personal information.
Pharming works by compromising the DNS server through DNS spoofing, DNS hijacking, and DNS cache poisoning. and is more difficult to accomplish.
Pharming is more difficult to accomplish for the attacker, and much harder for a user to identify. Since there is no baiting, and the redirect happens in the background of what appears to be a normal web session.
Both phishing and pharming are social engineering online cyberattacks and are devastating to individuals and organizations alike.
Best practices to prevent phishing and pharming
Both phishing and pharming are serious cyber threats to any organization today. Regardless of their differences, these cyber scams lead to the same consequence: the loss of confidential data for malicious use.
To secure your organization from phishing and pharming, follow these effective cybersecurity measures:
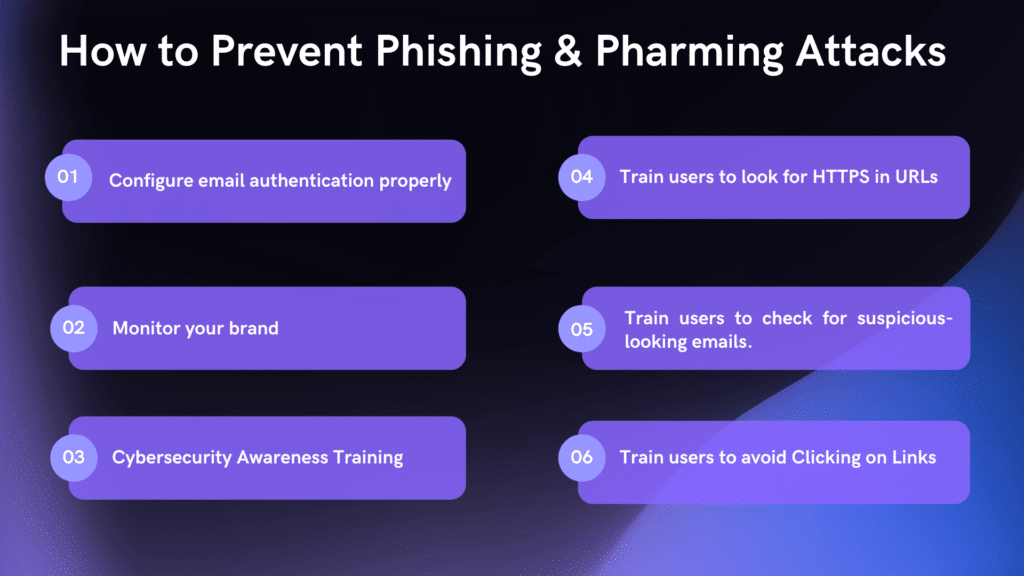
1. Configure email authentication properly
2. Monitor your brand
3. Cybersecurity Awareness Training
4. Train users to look for HTTPS in URLs
5. Train users to check for suspicious-looking emails.
6. Train users to avoid Clicking on Links
1. Configure email authentication properly
Why pay for recovering damages to cyberattacks when you can easily invest in the right cybersecurity solutions at a lower cost?
You can secure your email domain from unauthorized access with email authentication protocols like SPF, DKIM, and DMARC.
Take a look at the article below for more details:
2. Monitor your brand
Always keep track of how your brand is represented online.
Anti-phishing and fraud monitoring tools help identify any online copyright infringement activity against your organization’s website or application.
Also, monitor your postmaster@ role address, and review backscatter. Backscatter are emails sent on your behalf that have been rejected.
In addition, if you use DMARC, you will also see phish emails in the return address you have specified in your DMARC record.
3. Cybersecurity Awareness Training
We can’t ignore that employees are the most vulnerable link in the chain of cybersecurity. It is crucial to provide employees with proper Internet Security Awareness Training (ISAT) to identify potential cyber risks to strengthen this link.
4. Train users to look for HTTPS in URLs
While DNS spoofing generally doesn’t work on HTTPS websites, if a hacker manages to spoof a legitimate website and redirect a user, if they are aware of the attack vector, the phishing attack won’t be successful.
5. Train users to check for suspicious-looking emails.
Phishing emails often consist of suspicious-looking content, while less and less contain grammatical errors. Also, the source of the email address is unknown in most cases, so it is always better to cross-check any unfamiliar or unexpected email.
Don’t click on a phishing lure!
6. Train users to avoid Clicking on Links
Emails are the successful carriers of malicious attachments like links, document files, images, etc. Try to avoid clicking suspicious or unexpected email attachments, as they redirect users to fraudulent web pages and request personal information. Make sure to verify such emails on an incident response tool, so that they are not a target of any cyber attack.