What is Hijacking in Network Security?
Hijacking in network security is an attack, in which the attacker takes control of
What is Network Hijacking?
Network hijacking is a type of organizational hijacking that involves the unauthorized use of groups of IP addresses, known as ranges. Network hijacking includes IP hijacking or Route Hijacking.
Typical uses of these hijacked ranges include spam, phishing, pharming, and man-in-the-middle attacks.
If the cybercriminal acquired the ranges through a Regional Internet Registry (RIR), they will also often try to sell them after burning through them.
The consequences for organizations whose networks are hijacked are significant.
Are some networks more vulnerable to being hijacked than others?
There are several ways that cybercriminals can hijack your network, but they will always investigate suitable targets before they do.
Within all RIRs, there are ranges of unused registered IP addresses.
These ranges of IP addresses are unused and inactive, due to various reasons, including:
- Companies lose track of IP addresses assigned to them, forget about them, or otherwise decide not to use allocated IP addresses
- Companies going out of business or being acquired
How is IP hijacking accomplished?
There are three ways in which IP hijacking (Internet Protocol Hijacks) may be carried out.
They are: Malicious range announcements, Malicious peering connections, and Phishing for unused ranges
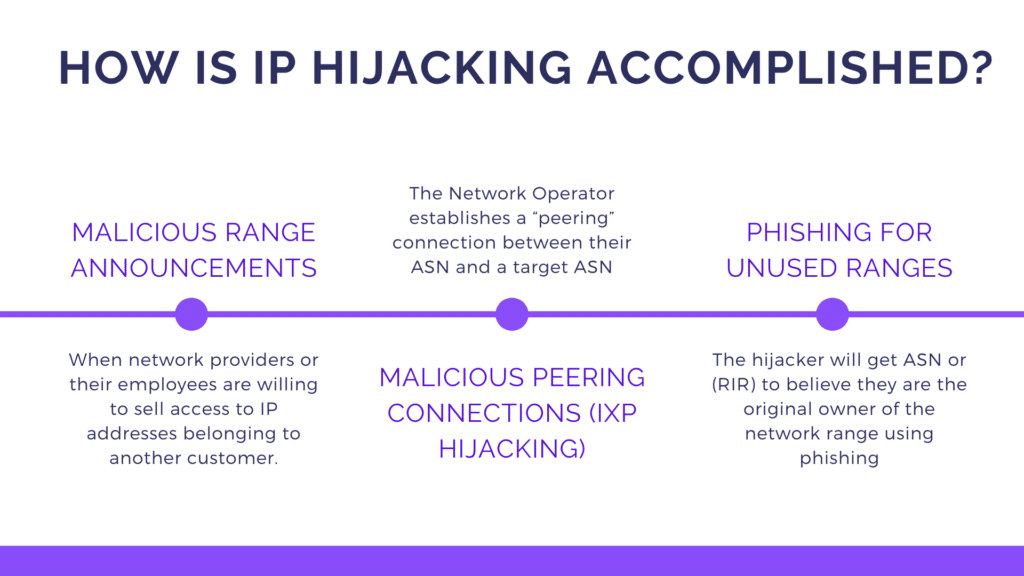
Malicious Range Announcements
Malicious Range Announcements occur when network providers – ASNs, managed by collocation/hosting providers/ISPs- or their employees are willing to sell access to IP addresses belonging to another customer.
By doing this, cybercriminals can use these otherwise unused IP ranges.
Malicious Peering Connections (IXP Hijacking)
An Internet Exchange Point (IXP) is where data between network operators is exchanged.
In an IXP hijacking, the Network Operator establishes a “peering” connection between their ASN and a target ASN, and announces hijacked ranges through the exchange. Since IXPs often do not track their exchanges for network abuse, it usually takes a long time to address problems, if at all.
Phishing for Unused Ranges
Another way hijackers gain control of target IP ranges is to use social engineering.
The hijacker will get ASN or the Regional Internet Registry (RIR) to believe they are the original owner of the network range using phishing.
The hijacker registers a domain that looks like the domain owner or gets an expired domain for a company that has gone out of business through a domain auction.
Once the hijacker has assumed the identity of the range owner, they will convince the desk that manages range assignments to update that network’s registration to include their new domain name or other information.
When the change is made, the hijacker will receive emails meant for the original range owner and communicate with the ASN manager or the RIR to update the target range to announce the range. In this phishing attack, the cybercriminal may provide the network operator or RIR with a Letter of Authority (LOA) with forged letterhead and signatures, impersonating the legitimate network owner.
BGP Hijacking
BGP hijacking or Route Hijacking is the illegal takeover of IP addresses by corrupting Internet routing tables used within the BGP (Border Gateway Protocol).
A hijacker will announce and reroute network traffic for smaller ranges of a network without authorization from the owner of those addresses. By announcing smaller ranges than the ASN, the smaller range will focus on routing over a larger network containing the range.
Yet, network traffic can also be rerouted back to the original network after the cybercriminal initiates a man-in-the-middle attack by listening, modifying messages, or inserting packets in the stream.
All these hijackings occur when you aren’t watching your network range assignments. If you aren’t monitoring how your Internet traffic is routed, your organization can’t prevent or immediately detect network hijacks.
When a network hijacking occurs, latency will increase because hijacked network flows rarely follow efficient routes and often traverse around the world unnecessarily.
So, monitoring latency and its impact on your users’ experience can help detect if your network has been hijacked. Also, if you track the BGP routes taken by your traffic, you can immediately detect any abnormal route change.
Other types of hijacking that affect organizations
While the primary focus of this article is Network Hijacking, other types of Hijacks also affect organizations.
We listed them below, so you were aware of these as well.
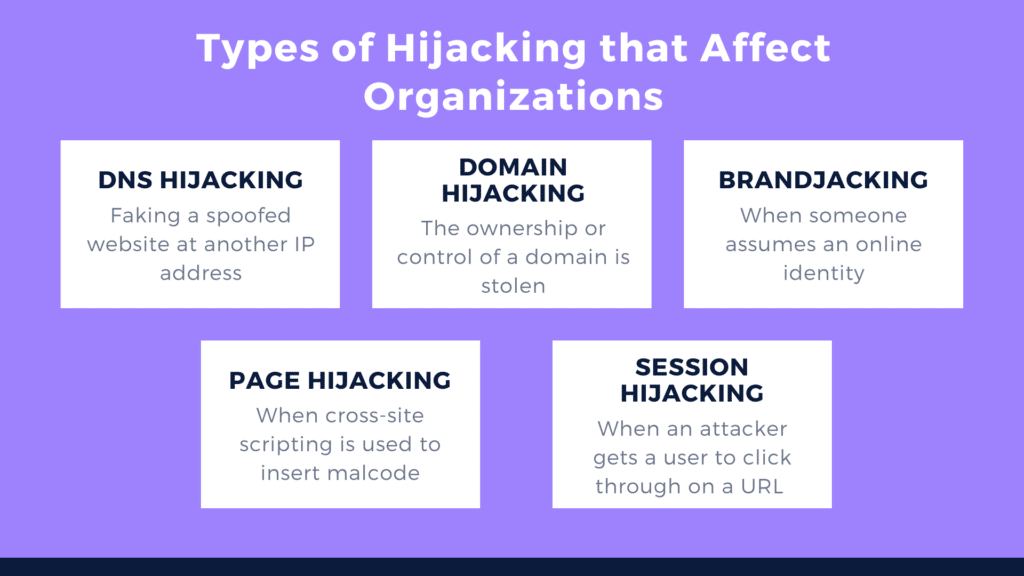
DNS hijacking
The domain name system (DNS) translates domain names into individual IP addresses hosted by servers.
In DNS hijacking, cybercriminals redirect all user web traffic, using a rogue DNS server, to a fake spoofed website at another IP address.
Users of a website experiencing a DNS hijacking attack are often unaware that they have arrived at a spoof of the site they intended to visit.
The unaware redirect often leads to the user divulging sensitive or personal information.
Domain hijacking
Domain hijacking occurs when the ownership or control of a domain is stolen from its rightful owner to another party.
The most common domain hijacking is done through a change in domain ownership. Hijacking, in this case, is similar to “phishing for unused ranges”, as it is an elaborate phishing attack or false cybersquatting claim.
Brandjacking
Brandjacking occurs when someone assumes an online identity; usually a famous person or brand. MarkMonitor coined the term.
The hijacker assumes a target’s identity on social media or buying domains in brandjacking.
Like cybersquatting, identity theft, and phishing, brandjacking is usually an attack that leverages a politician, celebrity, or business’s identity.
A brandjacking may take advantage of the known brand for financial gain and damage the reputation of its target for hostile, malicious, or political reasons.
Reverse domain name hijacking (RDNH) is the legal remedy to brandjacking.
It occurs when a rightful trademark owner attempts to claim a domain by making a cybersquatting claim against a domain name’s owner.
Larger corporations often use RDNH and famous individuals to defend their trademark and prevent libel or slander.
Brandjacking may be prevented if you put into practice several steps. You can take on these yourself or use a service like MarkMonitor to help you.
The steps are:
- Register Your Trademark.
- Invest in Brand-Related Domains.
- Invest in Social Listening Tools.
- Have a Crisis Management Plan.
Page hijacking
While cross-site scripting can be used in several ways, page hijacking occurs when cross-site scripting is used to insert malcode on the target web page and redirect its traffic to another web page on another website.
The page that the user is forwarded to contains spoofed content from the hacked page. The cross-site script is placed on a web application, a credit card form page, or log-in in the most severe cases. When pages are hijacked, the hijacker can also insert code on the hacked page that indicates it is temporary.
This lowers the web search ranking of the hacked page and increases the ranking of the spoofed page.
To protect most data sets from cross-site vulnerabilities, take the following two steps:
- Install a web application firewall
A web application firewall (WAF) can help in protecting against cross-site scripting attacks. It filters out bots and other malicious activity which often installed during the attack. Attacks are blocked before any script is executed.
2. Implement data validation by:
- Escaping user input: escaping converts data received from your web page and prevents the rendering of special characters, so they may not be interpreted in a malicious manner.
- Validating user input: treat anything that originates data outside your web application as untrusted and validate all the input data it provides.
- Sanitizing input data: review and remove unwanted data on an ongoing basis. Such data may include HTML tags or unusual characters that may be unsafe from the data.
3. Use web application scanning tools to detect security vulnerabilities and mitigate them as well as to detect page redirects.
Session Hijacking
A session hijacking attack occurs when an attacker guesses, confiscates, or gets a user to click through on a URL with a session-id the hijacker created and then gains unauthorized access to the target web server.
Web developers can help prevent session hijacking by using long session-id and session keys and encryption if they understand how session hijacking attacks occur and design to avoid them as they design web applications. These standard attack methods are:
Brute Force Session Hijacking
In a brute force session hijacking, the attacker guesses a session-id and uses it to steal the session. Successful brute force session attacks usually reflect repeat, short or easy-to-guess session keys and weak security.
Cross-Site Scripting Session Hijacking
A cross-site scripting session hijacking results from a hijacker locating a website or web server vulnerability.
In a successful cross-site scripting attack, the attacker injects malcode into web pages. The malcode will allow the hijacker to see the user’s session key in a man-in-the-middle attack and then steal the session.
Malware Session Hijacking
A malware session hijacking occurs when the hijacker tricks a user into clicking on a link that installs malware on their device.
The malware then searches for a session cookie on the user’s device and sends it to the hijacker, who can then steal the session.
Session Side Jacking
A session side jacking occurs when a hijacker has access to the user’s network traffic via a man-in-the-middle wi-fi attack.
The man-in-the-middle can search for session-ids and then hijack or steal the session using packet sniffing.
Session Fixation Hijacking
In a session fixation hijacking, the hijacker will send the user a link containing a session-id created by themselves.
That is, the hijacker fixes an anticipated session-id. An example might be fixing a session-id within an advertisement and asking the user to log in using that fake session-id in the link, allowing the hijacker inside.
Session hijackings occur because the hijacker can either guess the session-id, hack the session-id, steal a cookie, or trick the user into clicking on a URL and then logging in to a session that they preconfigured.
The best way to prevent session hijacking attacks is to use long random and expiring session ids and session keys.
Hijacking directly affects users too
Hijacking networks, brands, and web servers are devastating to any business.
These types of hijacks include browser hijacking, control hijacking, malware hijacking, and clipboard hijacking.
To help administrators with understanding these attacks, we will be publishing a future blog post, “Hijacking of individuals – what are the different ways hijacking occurs?”



