Ransomware attacks are no longer rare, targeted incidents. They are repeatable, automated, and profitable operations that scale across industries.
For CISOs, IT leaders, and infrastructure providers, this shift matters right now. Ransomware is moving faster than traditional defenses, exploiting gaps outside the enterprise perimeter and hitting organizations that thought they were “well protected.”
In this post, we break down why ransomware attacks are becoming more common, what has changed in the threat landscape, and how organizations can respond effectively when prevention fails.
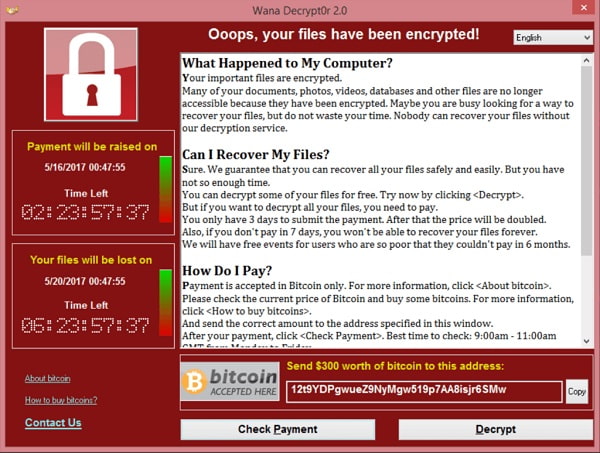
What Is a Ransomware Attack?
A ransomware attack is a type of cyberattack where attackers encrypt systems or data and demand payment, usually in cryptocurrency, to restore access.
A simple example:
- An employee receives a phishing email
- Malware executes after a click or credential theft
- Systems are encrypted or data is exfiltrated
- A ransom note demands payment within hours or days
Modern ransomware goes further by threatening data leaks, service disruption, or repeat attacks if payment is refused.
Why Ransomware Attacks Are Increasing So Rapidly
1. Ransomware Is Easy to Monetize
Cryptocurrency removed friction from cybercrime. Attackers can receive payments quickly, anonymously, and across borders.
This has transformed ransomware into a predictable revenue stream, not a one-off crime.
- Ransomware-as-a-Service lowers the skill barrier
- Affiliates split profits with developers
- Campaigns run continuously, not opportunistically
According to IBM, the average cost of a ransomware attack reached $4.54M, higher than most other breach types .
2. Attacks Start Outside the Enterprise Perimeter
Most ransomware does not begin with a firewall failure.
It starts upstream:
- Compromised ISP subscriber networks
- Abused cloud infrastructure
- Infected hosting environments
- Poorly monitored outbound email systems
This is a critical blind spot. Traditional security tools focus on what happens inside the organization, while ransomware operators exploit where attacks originate.
Abusix data shows that over 99% of enterprise-targeted attacks originate from ISP and access networks, long before they ever reach an endpoint .
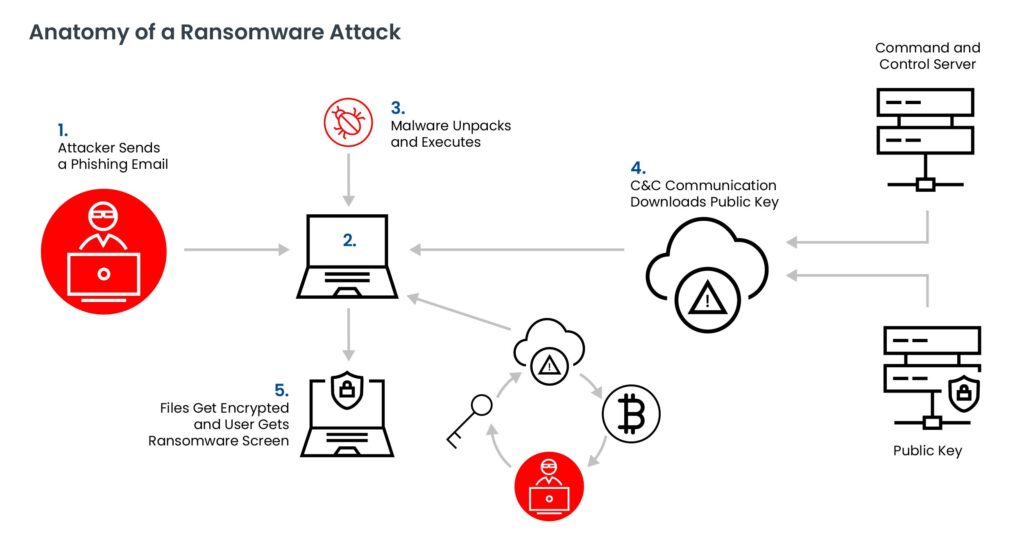
3. Email Remains the Primary Delivery Vector
Despite years of investment, email is still the most reliable ransomware entry point.
Why?
- Email infrastructure prioritizes delivery, not abuse prevention
- Legacy filters focus on content, not sender reputation
- Compromised accounts send “legitimate-looking” messages
Ransomware operators increasingly rely on infrastructure reputation abuse, not just malware attachments.
4. Automation Favors Attackers
Ransomware groups operate like SaaS companies:
- Automated scanning for exposed systems
- Scripted lateral movement
- Pre-built negotiation portals
- Timed pressure tactics
Meanwhile, many organizations still rely on manual triage, fragmented tooling, and slow abuse handling workflows.
The imbalance favors speed, and attackers know it.
Where Ransomware Risk Shows Up First
Ransomware risk usually appears in places teams underestimate:
- Outbound email infrastructure sending malicious links
- Poor IP reputation linked to previous abuse
- Unmonitored abuse reports from third parties
- Delayed takedown of infected systems
By the time encryption starts, the attacker has often been active for days or weeks.
How to Handle a Ransomware Attack Effectively
Ransomware response is about containment, coordination, and speed, not panic.
1. Isolate Systems Immediately
- Disconnect affected machines from the network
- Disable compromised accounts
- Stop outbound communication to command-and-control servers
Containment limits blast radius and prevents reinfection.
2. Preserve Evidence Before Remediation
- Capture logs, network flows, and abuse reports
- Preserve ransomware notes and indicators
- Avoid wiping systems prematurely
This data is critical for understanding where the attack originated and how it spread.
3. Communicate Early and Clearly
- Notify internal stakeholders
- Engage legal and compliance teams
- Prepare customer or partner messaging if needed
Delayed communication often causes more damage than the attack itself.
4. Address the Origin, Not Just the Impact
This is where many responses fail.
If infected infrastructure remains active upstream, attackers can:
- Re-launch the same campaign
- Target partners or customers
- Damage your network reputation
Stopping ransomware requires takedown at the infrastructure level, not just endpoint cleanup.
Tools and Approaches That Reduce Ransomware Impact
Guardian Mail
A connection-level email defense that blocks malicious senders before messages reach content filters. It neutralizes ransomware delivery at the SMTP layer.
Guardian Intel
Provides real-time visibility into abusive IPs, networks, and infrastructure used in ransomware campaigns, helping teams block threats earlier.
Guardian Ops
Automates abuse intake, triage, and takedown workflows for ISPs, hosting providers, and large networks, shrinking response time from days to minutes.
These approaches focus on shrinking the window between detection and takedown, which is critical when ransomware spreads automatically .
Common Ransomware Response Mistakes
- Treating ransomware as only an endpoint problem
- Ignoring outbound abuse signals
- Relying on manual abuse desk workflows
- Focusing on payment decisions before containment
Each delay increases cost, exposure, and repeat risk.
Why Ransomware Will Keep Rising Without Infrastructure-Level Defense
As long as attackers can operate freely from abused networks, ransomware will scale.
Defending against it requires a shift from isolated protection to collaborative, infrastructure-first mitigation, where victims, ISPs, and security teams close the loop together.
That shift is already underway, but organizations that delay it will remain easier targets.
Take the Next Step
If ransomware is becoming more common, it’s because attackers move faster than defenses.
👉 Contact us at https://www.abusix.com/contact-us to see how Abusix helps stop ransomware at the source, not just after the damage is done.
FAQ
Why are ransomware attacks increasing so fast?
Ransomware is profitable, automated, and easy to scale using abused infrastructure and cryptocurrency payments. Attackers face low risk and high reward.
Is ransomware mostly delivered through email?
Yes. Email remains the primary delivery vector, especially through compromised accounts and poor sender reputation controls.
Should organizations pay the ransom?
There is no guarantee of recovery, and payment often funds future attacks. Focus first on containment, evidence, and infrastructure takedown.
How can ISPs and cloud providers help stop ransomware?
By detecting abuse early, automating takedowns, and collaborating with victims to shut down malicious infrastructure quickly.
Additional Resources
- Email reputation and threat intelligence – https://abusix.com/email-threat-protection-solution/
- IBM Cost of a Data Breach Report – https://www.ibm.com/reports/data-breach
- NIST Ransomware Guidance – https://www.nist.gov



