Introduction
Have you ever stopped to wonder how bulletproof your email inbox is? Email is a massive part of our daily lives, which unfortunately also means it's a hotspot for cybercriminals and baddies, from phishing schemes to nasty ransomware attacks. In this article, we're peeling back the curtain on the hidden risks of email. More importantly, we'll walk you through some rock-solid strategies to up your email security game. Keep your digital correspondence safe and sound with the correct personal information here. Let's dive in.
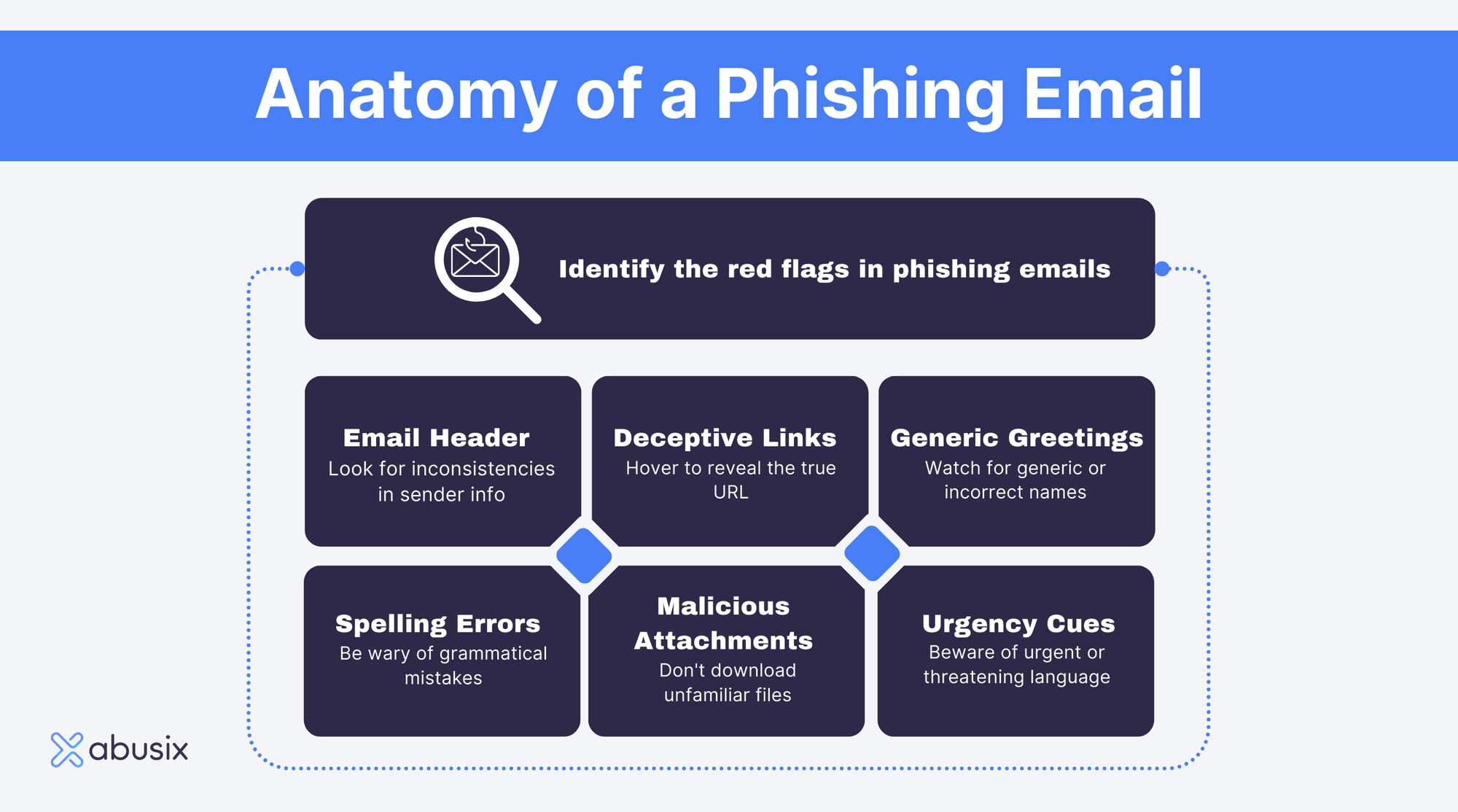
Common Characteristics of Phishing Emails

Do you know how impersonators try to mimic celebrities? Phishing emails do the same thing, pretending to be from companies or people you trust. The good news is that these scammer" phishing emails often have "tells," little signs that give away their true nature. Spotting these red flags can be your first defense against falling for a serious scammer. Think of it as your digital detective, equipped to discern the good from the bad. Ready to get clued in?
Look Out for Language Glitches
- Typos and Grammar Mistakes: Legit companies have editors for their emails. So, if you spot language errors, your scam radar should start beeping.
Tone and Greeting
- Generic Hello: If the email says "Dear Customer" instead of your name, be wary. Authentic messages usually make it more personal.
- False Urgency: Got an email pressing you to act fast or risk losing your account? Take a breath. Scammers love making you panic, so you'll make mistakes.
Red Flags in Content
- Asking for the Keys to the Kingdom: No reputable organization will ask for your password or credit card info through email. If they do, it's probably not them.
Be a URL Sleuth
- Funky Web Addresses: Hover over links to reveal their actual URL. If it's even a bit off, like "bankofarnerica.com" instead of "bankofamerica.com."
- Insecure Links: Real websites for things like your bank will use HTTPS, not just HTTP. The 'S' is for security (and 'smart' if you catch it).
Sketchy Attachments
- Odd File Types: See a weird file extension like ".exe" or ".jar"? Those can execute harmful code. Wait to open them.
- Unexpected Attachments: If you didn't expect an attachment, don't touch it. Even if it's pretending to be a holiday e-card from Aunt Karen.
Deceptive Clickables
- Misleading Links: Sometimes, the text or button you see doesn't match the URL it leads to. Always hover over it first to see where it goes.
Getting the hang of spotting these telltale signs boosts your defenses against phishing attacks. Think about it: You're protecting your info and helping secure sensitive information in your workplace or household. It's like you're the neighborhood watch but for spam in your phone or inbox. So give yourself a pat on the back. You're becoming the best defense against phishing messages, malware, and data breaches!
Advanced Phishing Techniques

Alright, you've got the basics to report phishing now, but let's talk about the next level: the crafty, James Bond-level phishing messages and techniques. These phishing messages aren't your everyday phone scams; they're custom-built to trick even the most cautious among us.
- Ultra-Personalized: These emails don't just know your name; they know your job, your friends, and even where you had lunch last week, thanks to social media snooping.
- Sneaky Filters: Because they're so well-crafted, these messages often dodge your email's spam catcher.
Clone Phishing
- Déjà Vu: This technique clones an actual email you've gotten before, swaps out the links or attachments with harmful ones, and hits resend.
- Trust Trap: You think it's a follow-up or reminder, so you're more likely to click.
Whaling
- Big Fish: The scammers are after the bosses or anyone with the keys to the financial kingdom.
- Multi-Level Scheming: They don't just email; they might call or text to lay the groundwork for the scam.
Credential Harvesting
- Login Lures: You're tricked into entering your details on a fake but convincing login page.
- Two-Factor Feint: Some even know how to get around your two-factor authentication. Yikes!
Watering Hole Attack
- Familiar Territory: Attackers compromise a site you often visit and lie in wait.
- Trap Set: When you log in, they snag your info or infect your device.
- Web Hijacking: Instead of tricking you into a fake site, they redirect the actual site's traffic to their fraudulent version.
- Global Snare: This one's enormous; it can catch anyone visiting the website.
Okay, so how do we stop these ninjas of the cyber underworld? Individual smarts go a long way, but tech safeguards are your digital armor against these advanced threats. We'll dive into those must-have tools to keep your inbox a fortress. Stay tuned!
Detection Mechanisms

Let's get into how technology is leveling up to outsmart phishers. Trust me, this is your digital toolkit for staying one step ahead.
Signature-based Detection
What it is: Think of this as the 'mugshot' method. There's a database of known phishing email patterns or "signatures." If an incoming phishing message or email looks like one of those baddies, it's flagged or sent straight to the victim in the digital dungeon.
Limitation: The catch? It's only good for catching the crooks it already knows about. New scams? Not so much.
Anomaly Detection
What it is: This method is dynamic and super smart. It uses machine learning to establish what a typical email should look like.
Why it's cool: If an email or message strays from this 'normal' behavior, it's flagged. This approach is better at catching new, clever phishing emails, messages, potential targets, and tactics than the signature-based method.
User Reporting and Feedback Loops
What it is: We're all human; sometimes, even machines miss a trick. Many companies offer reporting tools for employees to flag anything fishy.
Why it's important: These human reports often lead to rapid updates in security protocols. It's like a feedback loop that makes the whole system smarter and faster at catching new malware threats.
So, identifying scams is just one piece of the puzzle. The real win is preventing these sketchy emails and text messages from even making it to your inbox. Because let's face it, prevention beats cure every time. We'll dive into the proactive steps you can take to keep personal or financial information about you and your organization safe.
Protective Measures Against Phishing Emails

Alright, so you get that no system is bulletproof. That's why being proactive is your best defense against phishing attacks. Let's look at some hands-on tactics.
Employee Training and Awareness Programs
The Rundown: Use training to defend against a phishing email or attempt. A well-designed program teaches everyone the dos and don'ts, helping them spot the phishing scam or emails like a pro.
The Plus: Have you ever heard of simulated phishing attacks? They're mock exams but for phishing attacks. They test how well employees can spot scams, spam, and malware in real time and offer teachable moments immediately. Talk about learning by doing!
Email Filtering Solutions
The Lowdown: These are your cyber criminals and bouncers, keeping the bad stuff at bay. Some even use machine learning to improve over time at recognizing shady emails, text message messages, and passwords.
The Edge: These solutions don't just skim through suspicious emails; they look deeply at links, attachments, and even the email's text to spot potential threats. If they find something risky, they'll quarantine the email so it can't do any harm.
Incident Response Plans for Phishing Attacks
Need to Know: A game plan is essential if a severe phishing attack, email, or attack does not slip through. This is your incident response plan.
The Payoff: defines what to do to minimize damage, from isolating compromised systems to letting stakeholders know what's up. A well-executed plan is your ticket to reducing downtime and saving face.
So now you're armed with knowledge and eager to ramp up your email security. But how do you pick the right tools for the job? Don't sweat it; next, we'll review the key things to look for when shopping for an anti-phishing solution.
Evaluating Anti-Phishing Tools
Choosing the right anti-phishing tool might feel like navigating a maze, but fear not! We're here to break it down for you and help you make an informed decision. Let's dive into what you should be on the lookout for.
In-house vs. Third-Party Solutions
It's Decision Time: When it comes to anti-phishing tools, you've got two main paths. Building your in-house solution gives you the keys to the customization kingdom, but it's like taking care of a high-maintenance pet. On the flip side, third-party solutions are like hiring a pro; it's cost-effective and comes with a wealth of data to supercharge their defenses.
Feature Checklist
The Essentials: Your ideal anti-phishing tool should be a Swiss Army protection knife. That means it should cover all the bases—signature-based and anomaly detection, top-notch email filtering, text messages and message alerts, and reporting features. Think of it like having a security team that never sleeps.
Bonus Points: Some tools even offer threat intelligence feeds, adding an extra layer of security to sensitive data. When considering these features, match them up with your specific needs and the risks you face.
ROI of Anti-Phishing Solutions
Value Beyond Money: Don't just measure success in dollars and cents. Your anti-phishing solution's return on investment (ROI) is about more than financial gains. It's also about protecting your brand's reputation, earning customer trust, and staying on the right side of the law.
Worst-Case Scenario: Remember, skimping on your social media security and protection against malware can lead to hefty fines and a hit to your social security and bottom line. It's like not investing in security for your online or bank accounts—it's just not worth the risk.
Now that you know the right tool, let's pivot and explore the legal side. We'll delve into the regulations and legal obligations shaping the anti-phishing world. Stay tuned!
Regulatory Compliance and Legal Implications
Phishing is more than a social security or bank headache; it's a legal minefield, especially for businesses. You've got to be on top of rules like the GDPR and know your legal options if a phishing attack hits a bank, website, or you.
Staying on the Right Side of GDPR
If you're dealing with folks in the European Union, GDPR (General Data Protection Regulation) is a big deal. Slip-ups in protecting users' personal and financial info can lead to data breaches, and trust us, the fines under GDPR are no joke. So, the smart move? Invest in top-notch anti-phishing tools to protect and keep your users' data fortress unbreachable.
Don't Forget Other Rules
GDPR is just one player on the field. There's HIPAA in healthcare, and if you're handling credit card payments, PCI DSS has covered you. Each rule has its security must-dos and the penalties for dropping the ball. Let's say it's more than a slap on the wrist. You're looking at heavy fines and a massive hit to your reputation.
Why You Should Care
Protecting users of passwords, banks, and other accounts against spam and phishing is more than just a "best practice." It's often the law. With cyber rules getting stricter, compliance isn't optional; it's mandatory.
Your Legal Game Plan
Say a phishing website attack hits you; what next? Legal action against these online con artists is possible, but it can be tricky because the world is a prominent place with different rules. Still, a solid legal strategy is part of a more effort and well-rounded defense against cyber criminals and phishing website campaigns.
Future Trends in Phishing
Phishing attacks are like that villain in a movie that won't go away. They're adapting, evolving, and coming up with new tricks. So, how can you stay ahead of the phishing attack curve?
AI: Not Just Hype, But Your New Best Friend
Artificial Intelligence (AI) and machine learning are total game-changers for your own phishing campaigns and scam detection. What's the takeaway for you? If you're shopping for anti-phishing tools, ensure they have AI or machine learning capabilities. They can process tons of data in real time, recognizing phishing scams that human eyes might miss. So, consider investing in these advanced technologies to keep your security robust.
Don't Forget Your Smart Fridge Could Get Phished
The Internet of Things (IoT) isn't just about smart speakers and watches anymore. Everything from your fridge to your phone to your thermostat is getting "smart," but their security often isn't up to par. To take action, ensure your IoT devices have updated firmware and enable two-factor authentication. Make IoT security part of your larger anti-phishing plan to close any loopholes.
Stay Informed to Outsmart, the Scammers
Phishers constantly adapt, using techniques like polymorphic phishing emails to bypass your defenses. How can you beat them at their own game? Education and regular training are your best tools. Schedule ongoing security awareness sessions for your team and update everyone on the latest threats. Real-world simulations can also help reinforce the training and keep your staff sharp.
The bottom line: phishing threats are advancing, but you can still stay ahead. Investing in AI-driven tools, securing all your connected mobile devices, and educating yourself will set you up for a more robust defense. It's all about taking proactive steps, not just reacting when things go wrong.
Conclusion
So, are we doomed to be perpetual victims of email phishing scams? Not quite. Think of this as an ever-changing game of chess. They move; we counter. We can corner our cyber adversaries by embracing a cocktail of cutting-edge tech, our social media smarts, and a culture of continuous learning.
Remember, the evolution of phishing tactics is not a sign of defeat but a call to arms. We have the tools, financial information, the intelligence, and the collective will to prevail. So, if you want to reduce the number of phishing emails blocking your inbox, you should book a demo of Abusic Mail Intelligence today.